Detect and fix Active
Directory and Azure
Entra ID vulnerabilities
with one click
They trusted in us










AI-powered Engines
continuously detect, remediate, and protect your identity environment.

Identity Hygiene
Continuous assessment of AD & Entra ID posture.
Threat Detection
Real-time intelligence based threat hunting.
Prompt Remediation
Continuous assessment of AD & Entra ID posture.
Disaster Recovery
Complete capability to restore identity fabrics.
Recent data reveals escalating identity security threats
This highlights the urgent need for robust identity protection and zero-trust security
measures in modern infrastructure.
93% of Organizations
Had Two or More Identity-Related Breaches in the Past Year
— Cyber 2024 report
60% of Incidents
Identity-Based Attacks Account for 60% of All Cyber Incidents
— Cisco Talos 2024 report
Most identity breaches don’t start with advanced malware - they begin with silent, unresolved identity weaknesses
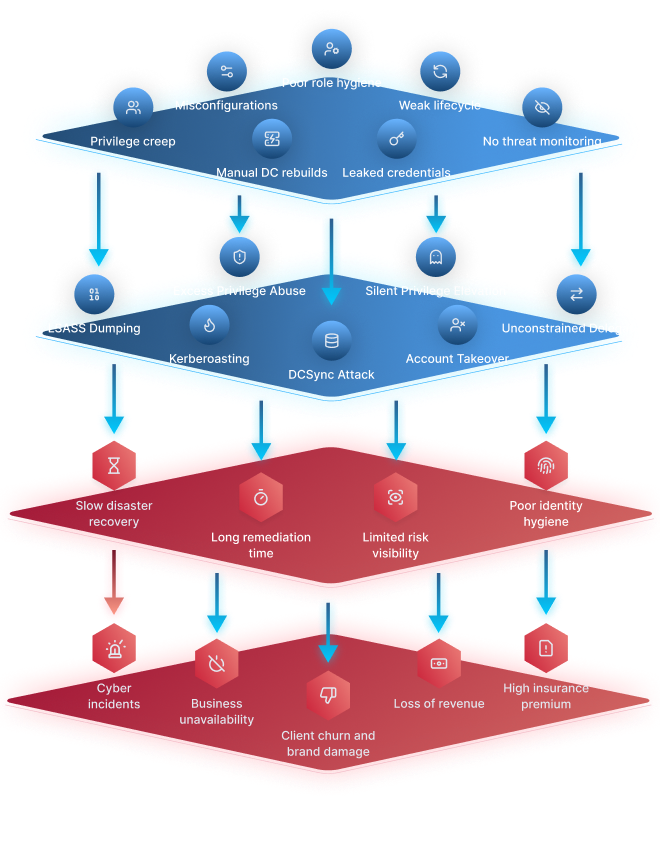
Without MRI
With MRI
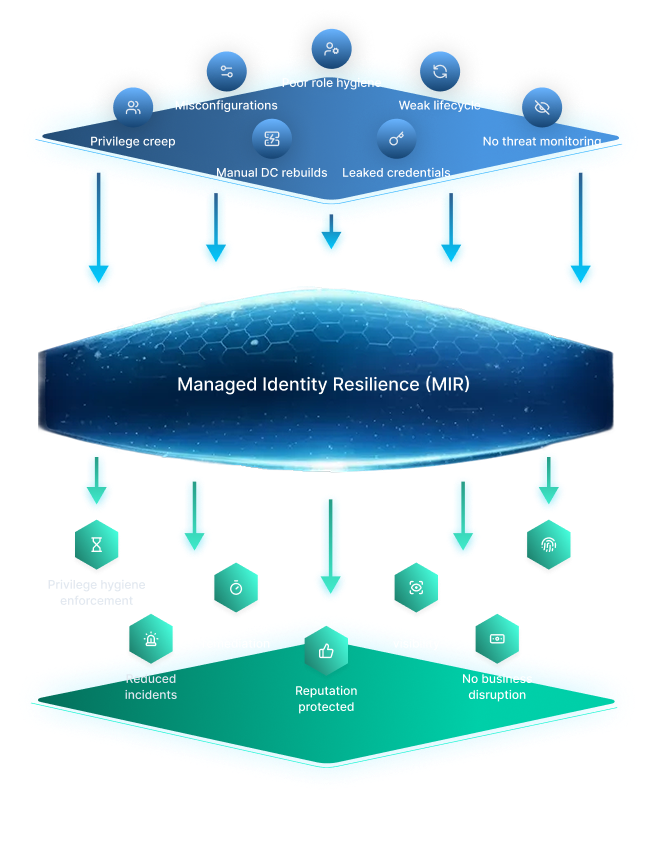
Managed Identity Resilience (MIR)
Managed Identity Resilience (MIR) helps organizations with Active Directory and Entra ID users reduce identity breach likelihood by up to 90% in just 30 days through a fully managed, SOC-backed detection, remediation, and response service – without the cost or complexity of managing internal tools, licenses, or specialist resources.
MIR Essential
Foundational IDENTITY Risk Reduction
For organizations that want fast, measurable identity risk reduction without
operational overhead.
Best Fit
Teams needing visibility & clear direction.
Included Outcomes
- Immediate risk reduction
- Full AD & Entra ID visibility
- Remediation ownership
Core Inclusions
Identity Exposure Detection
Continuous scanning of AD & Entra ID for:
- Privileged account hygiene issues
- Weak authentication & MFA gaps
- Misconfigured conditional access
- Legacy protocols & risky auth methods
- Stale, orphaned, and over-privileged accounts protocols & stale accounts.
Guided Remediation
- Assisted remediation and guidance
- Change instructions provided
- Customer executes changes
Monitoring & Reporting
- Continuous automated monitoring (24×7)
- Monthly Identity Risk Report
- Baseline vs current risk comparison
Most Popular
MIR Advanced
Proactive Detection & Response
For organizations that want continuous protection and faster risk reduction without
manual effort.
Best Fit
Security-mature IT teams & Compliance-driven orgs.
EVERYTHING IN ESSENTIAL, PLUS:
Automated Remediation
SOC-approved auto-fixes for:
- Privilege creep
- MFA enforcement
- Risky account states
- Conditional access misconfigurations
Advanced Threat Detection
Detection of:
- MFA misuse
- Lateral movement indicators
- Credential abuse & anomalous logins
- OAuth abuse indicators
SOC-Led Alerting
- Active alerting
Operational Reporting
- Monthly technical report
- Quarterly executive summary
- Risk reduction trend analysis
SOC Coverage
- 24×7 monitoring
- Defined response SLAs
MIR Elite
Full Resilience & Breach Readiness
For organizations that want identity treated as a critical risk surface — not a
configuration task.
Best Fit
Regulated industries, CISOs & those needing assurance.
EVERYTHING IN ADVANCED, PLUS:
Adversary-Aware Monitoring
- Attack path analysis (AD → Entra ID)
- Detection mapped to real attacker TTPs
- Monitoring for:
- Living-off-the-land abuse
- Privileged access misuse
- Identity persistence techniques
Breach Readiness & Recovery
SOC-approved auto-fixes for:
- Identity incident playbooks
- Rapid identity containment workflows
- Privileged access lockdown scenarios
- Identity recovery guidance
Executive & Board Reporting
- Monthly executive dashboard
- Identity risk KPIs
- Breach likelihood trend
- Audit-ready evidence packs
Dedicated SOC Experience
- Named SOC lead
- Priority response SLAs
- Monthly strategy & posture review
The Outcome
Daily
- Identity alert monitoring
- Risk drift detection
- Auto-remediation
execution
Weekly
- Risk posture review
- Remediation backlog mgmt
- Threat indicator review
Monthly
- Customer reporting
- KPI trend analysis
- Executive summary creation
Quarterly
- Strategic posture review
- Attack surface evolution
Package Comparison

How to reduce identity breach likelihood by up to 90%, in just 30 days
MIR helps mitigate these issues
Slow disaster recovery
Long time to remediate
Limited risk visibility
Poor identity hygiene
The Cost of Inaction
Every day without automated identity protection expands your attack surface – often in ways you can’t see.
Over 600 million identity attacks target AD and Entra ID environments daily. Even one overlooked misconfiguration can weaken your defenses and slow recovery after an incident.
- How long could the business operate during a directory outage?
- What would a breach do to customer trust?
- How much would one incident increase insurance costs?

Ready to Move from Risk to Resilience?
Take the first step with a complimentary baseline assessment
