Majority of cyber-attacks make their way in through external assets.
The dominating reason behind this is lack of visibility of these external risks.
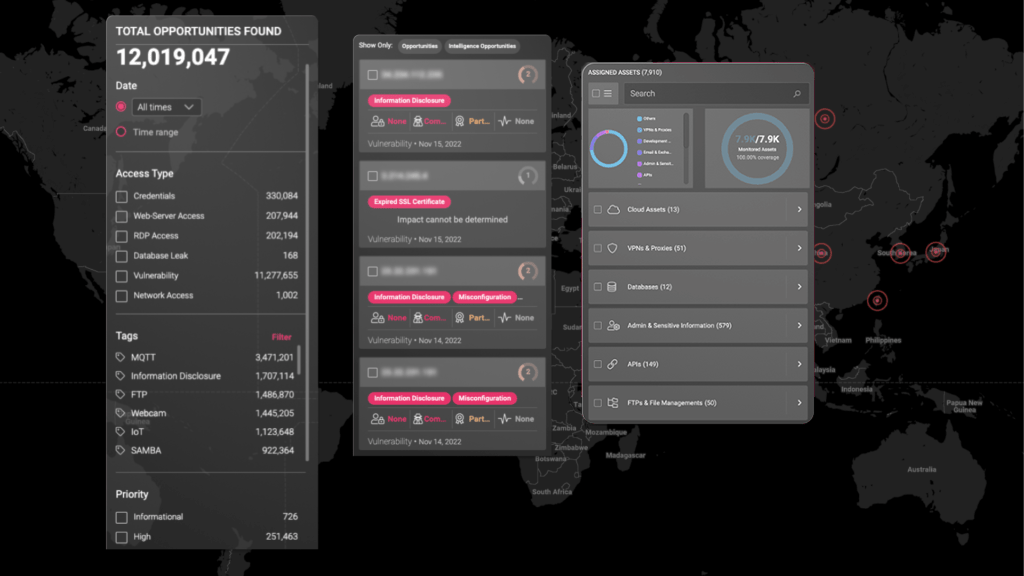
We bring the world’s first and only external asset exploitation simulation with unmatched scanning depth, to accurately identify vulnerabilities, and AI powered engine to analyse, prioritise, report and recommend resolution.
Leading to instantly and significantly improving your ability to see and defend against business-critical cyber threats.
This technology:
- automatically discovers all your external assets
- finds vulnerabilities and misconfiguration
- simulates sophisticated exploitation of those findings
- provides a detailed report and a curated list of remediation recommendations -- only with the most practical and actionable fixes.
- it also constantly crawls internet and Dark web to detect threats like compromised credentials and leaked data.
- is Agentless and can be setup in minutes
Take a complementary brand security test
Which brand name would you like assessed for brand security?
Lack of continuous automated exploitation of vulnerabilities, and identification of threats usually creates cyber defence blind spots. Also, without the automated and prompt analysis, reporting, and remediation recommendations, cyber teams struggle to find the time to accurately and promptly distinguish between false positives and real risks, and mitigate those risks. As a result, below risks could materialise:
- Data breach and unauthorised deletion
- Ransomware attacks
- Loss of revenue
- Brand damage
- Loss of customer trust
- Legal and regulatory fines
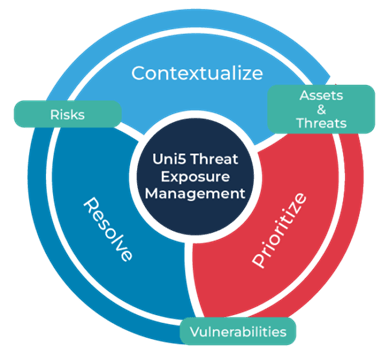
Gartner suggests that Continuous Threat Exposure Management (CTEM) allows enterprises to continually and consistently evaluate the accessibility, exposure, and exploitability of an enterprises digital and physical assets.
This technology will allow you to automatically and proactively identify and validate the following threats and vulnerabilities against all your external assets, along with the most contextual solution recommendation to fix them:
-
Assets’ Misconfigurations – E.G., Accidental API Release Without Proper Authentication, Unintentional Exposure Of Cloud Storages, Etc -
Assets’ vulnerabilities – E.G., Highly Exploitable Ports, Highjackable Subdomain(s), And/Or Broken Certificate Trust Chain, Etc -
Compromised Accounts And Sensitive Breached Data – E.G. Compromised Authentication Details, Or Leaked Source Code -
Impersonation And Phishing Attack – E.G. Impersonation Of Your VIP Staff's Social Media Account, Or A Web Site That Is Actively Trying To Phish Your Business -
Brand Abuse – E.G., Unauthorised Reseller, Counterfeit Operator, Fake Job Posting, Fake Mobile App, Etc.
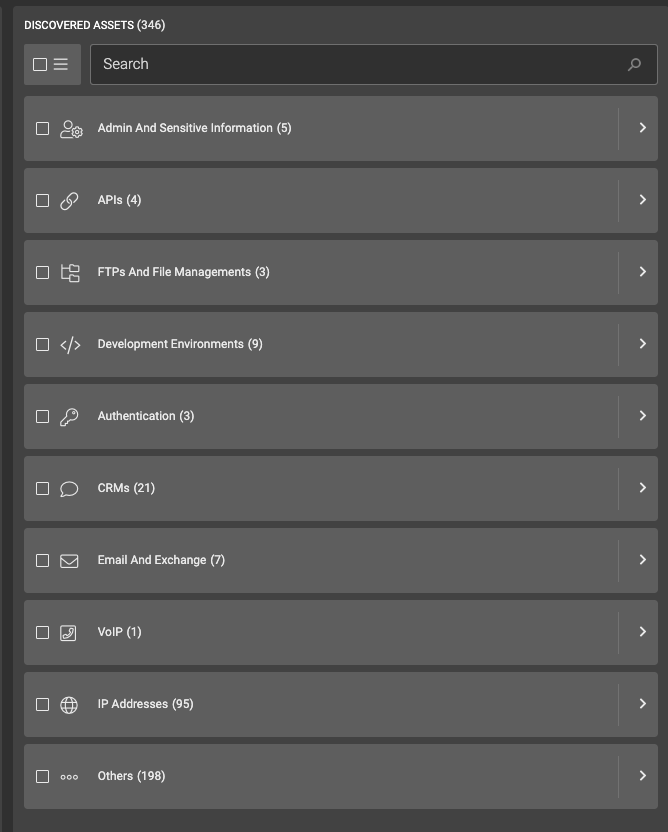
The type of assets covered:
- Admin And Sensitive Information (5)
- APIs (4)
- FTPs And File Managements (3)
- Development Environments (9)
- Authentication (3)
- CRMs (21)
- Email And Exchange (7)
- VoIP (1)
- IP Addresses (95)
- Others (198)
Take a complementary brand security test
Which brand name would you like assessed for brand security?
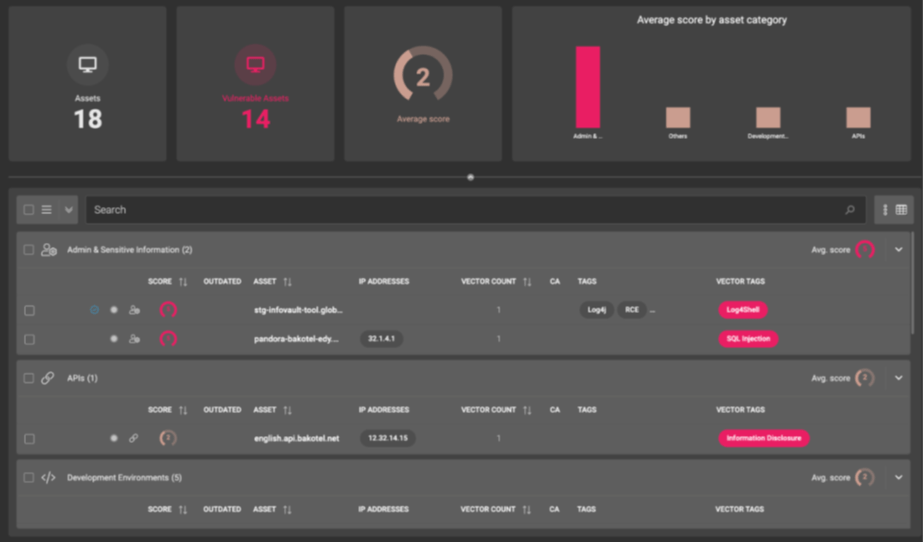
Asset discovery:
- Starting from a single user input: organization name, domain, IP, etc.
- Automatically maps assets, subsidiaries & supply chains
- Automatically assigns discovered assets into logical categories (APIs, Databases, CRMs, etc.)
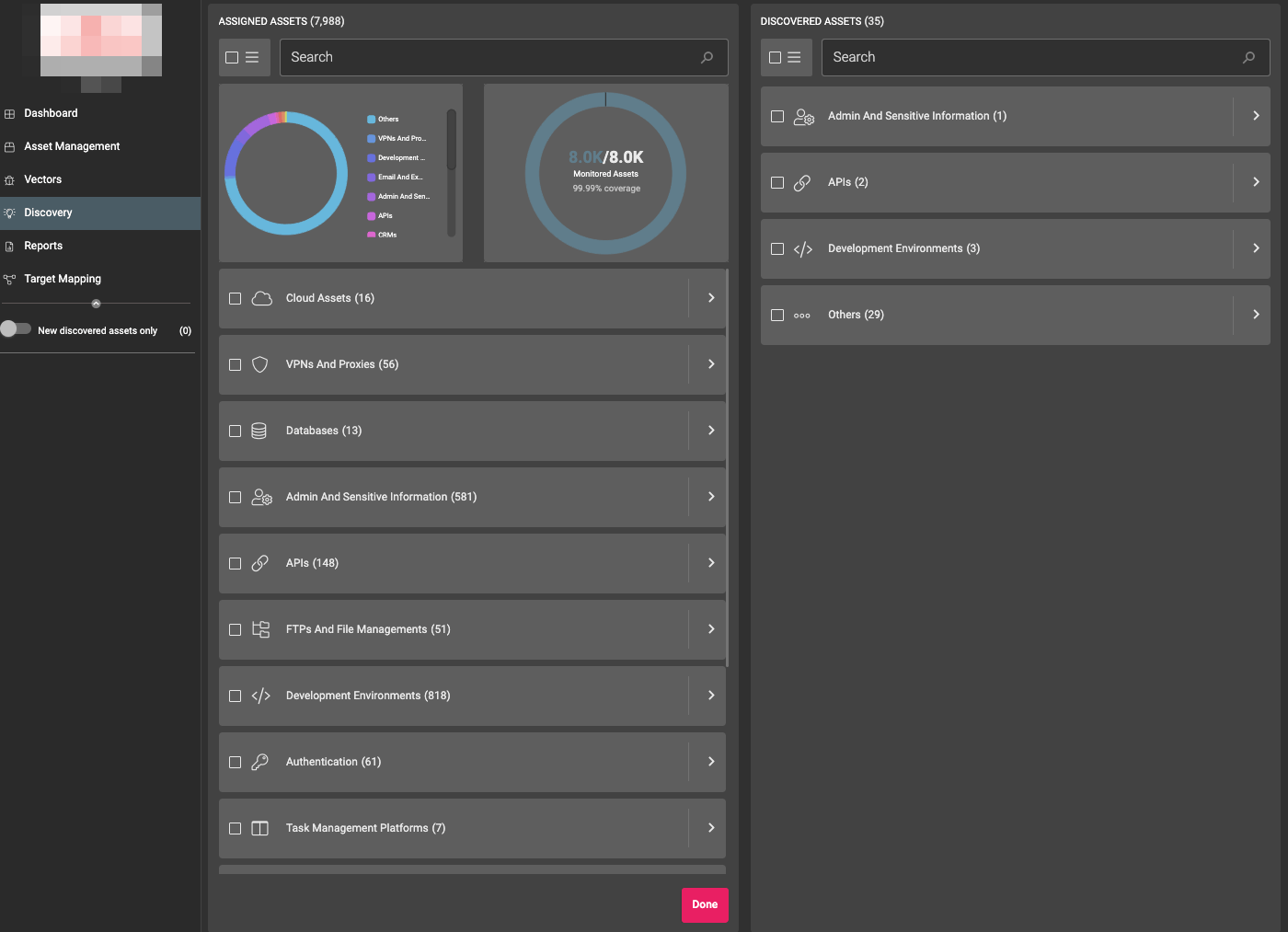
Asset Management:
- Automatically get insights on your assets without any manual work required
- Easily identify outdated assets and act
- Combine automated system generated tags with custom tags
- Validate your security control coverage with ease (i.e: Assets covered by WAF)
- Monitor assets for accounts that are sold in cybercrime communities
Continuous Attack Vectors Scan and Monitoring:
- Scanners are constantly updated with new vector types and technology coverage (new CVEs & techniques added daily)
- Proof of Concept included with every vector, confirming the validation and eliminating false positives
- No SOC overhead by leveraging rotating proxies to avoid WAF & detection by other controls no whitelisting required
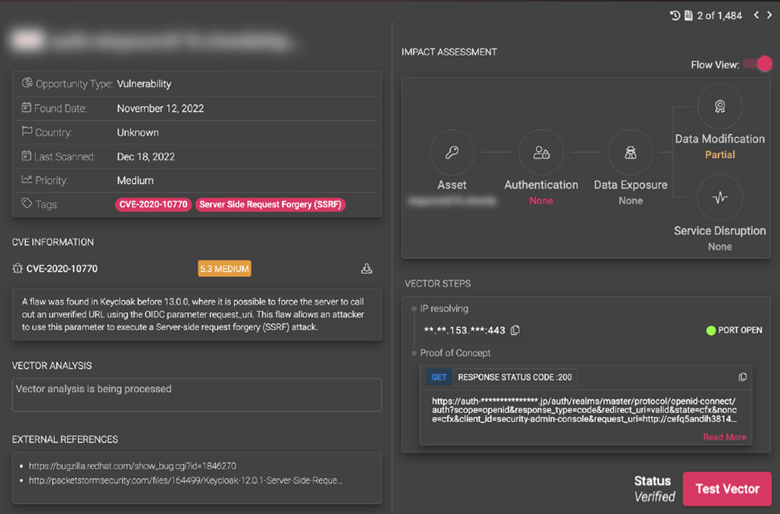
Actionable Remediation Solutions:
- Detailed remediation steps for every vector based on MITRE & NIST best practices
- Proof of Concept (Simulated Red Teaming) with every vector, allowing you to easily reproduce and emulate every vector
- External references for every vector and deep, detailed response analysis
- Context aware vector prioritization
Actionable Remediation Solutions:
- Detailed remediation steps for every vector based on MITRE & NIST best practices
- Proof of Concept (Simulated Red Teaming) with every vector, allowing you to easily reproduce and emulate every vector
- External references for every vector and deep, detailed response analysis
- Context aware vector prioritization
Take a complementary brand security test
Which brand name would you like assessed for brand security?

How it works:
- You provide us with the brand name to protect (Main domain)
- We automatically discover all your external assets - no installation or integration required
- We identify threats to, and vulnerabilities in your assets, perform simulated red teaming to measure their exploitability and will prioritise the risks accordingly
- We provide you with the most actionable fixes to proactively mitigate risks
- We continuously monitor your assets for threats and vulnerabilities
- We integrate with your management and monitoring solutions to provide you with the complete risk visibility and actions
