Knowing your security posture requires
answering these two questions:
Are your current security
controls effective & tested?

Do you have blind spots
in your protection measures?
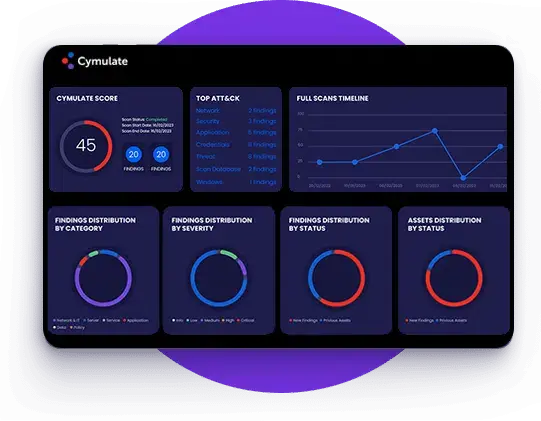
Without continuous end-to-end testing, the efficacy of an organization’s security posture remains unvalidated.
Majority of these validations are done through penetration testing which only provides a point-in-time snapshot of gaps.
In past it would’ve taken an enormous amount of resources to achieve continuous validation of security controls. Today, you can access it for a fraction of the cost, executed automatically and continuously!
Introducing Cymulate...
an automated, continuous end-to-end security testing platform – the only security validation platform you’ll ever need to validate and optimise your security people, processes and technology controls
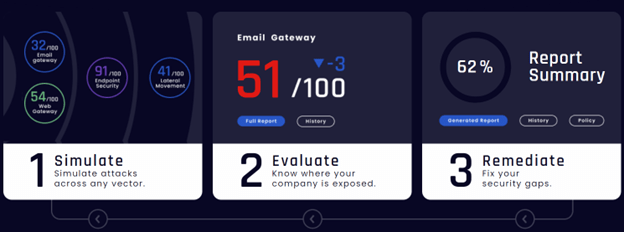
- Lightweight agent, running on a single machine
- Safely perform attack simulations in your environment
- Allows you to choose which attack vectors you wish to simulate
- Takes less than 5 minutes to set up
- Provides immediate actionable insights on your security posture
Get a FREE demo and a trial
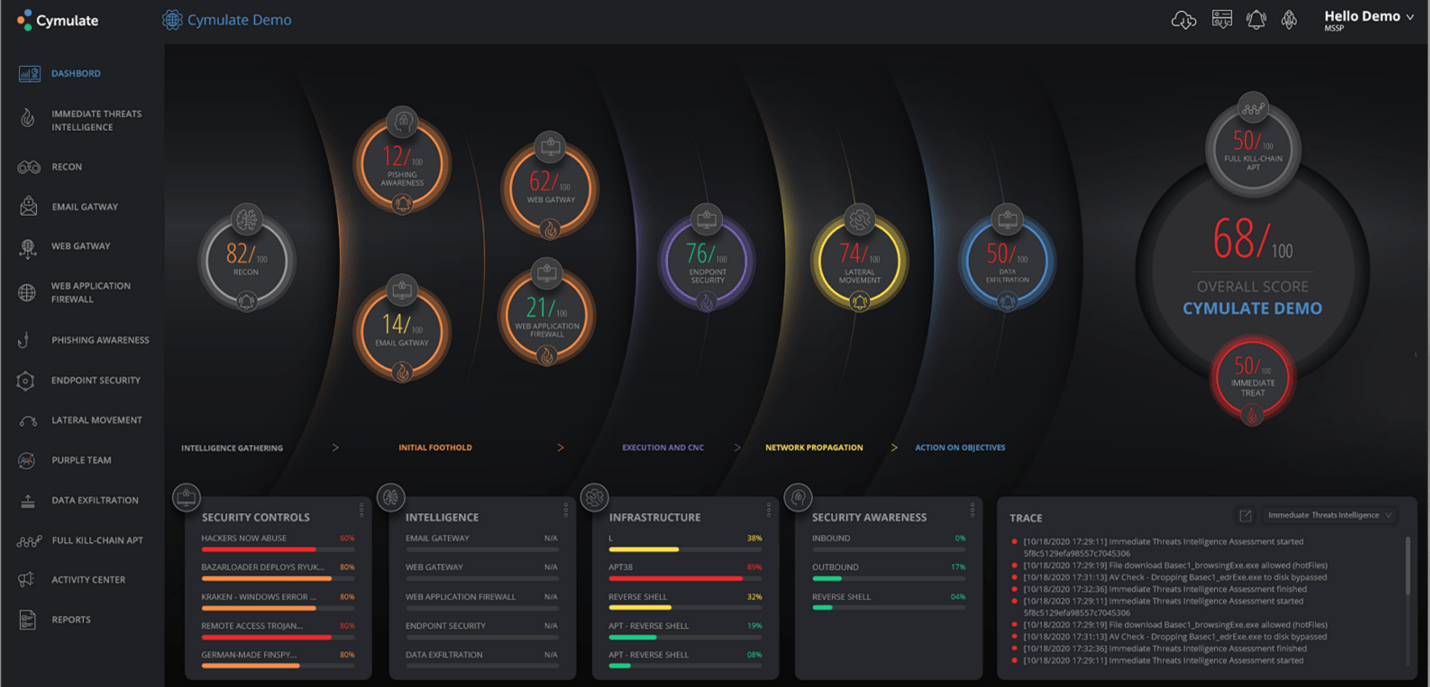
Threat Simulation Modules
Attack Surface Management:
It discovers application and infrastructure vulnerabilities, highjack-able sub-domains, web misconfigurations, open ports, leaked credentials, compromised passwords, Darknet presence, compromised employee emails, and other exploitable intelligence that an attacker may use to their advantage.
Benefits:
It continuously scans the internet for information that a malicious actor can find and use before launching an actual attack campaign. – Proactive measure against threats and attacks
Email Security Validation:
It will validate email security policies and protection capabilities against email attacks, by sending thousands of emails with attachments containing ransomware, worms, Trojans, or links to malicious websites.
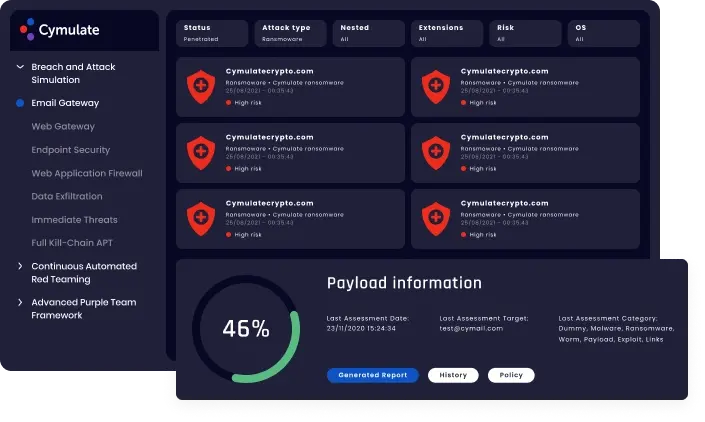
Benefits:
Reveal malicious email constructs trying to bypass your organizations’ first line of defence and reach your employees’ inbox.
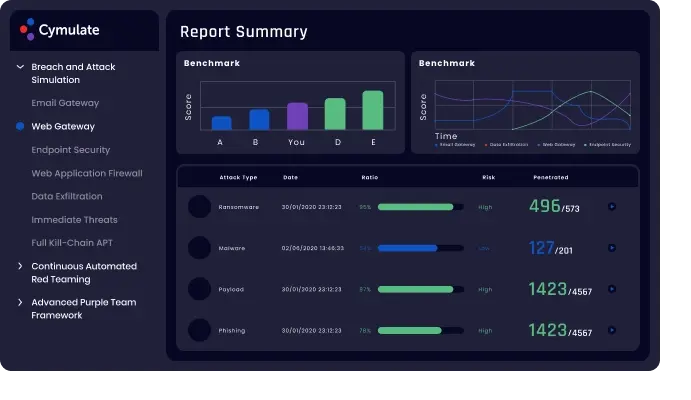
Web Security Validation:
It will validate web security and proxy policies and settings in protection against compromised or malicious web sites that download malware to the victim’s device, inject malicious code into legitimate informational forms and ecommerce carts, or scams and malicious URLs
Benefits:
Protect your staff while browsing internet, against malicious web sites.
Endpoint Security Validation:
Challenge the endpoint security solutions to assess their effectiveness, measure their policy and configuration, and that they are indeed protecting your organization’s critical assets against the latest attack methods.
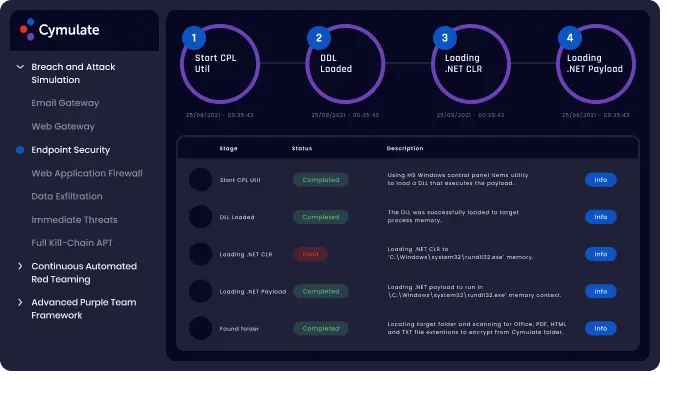
Benefits:
Find the gaps in your endpoint security through real world attack scenarios, measure their ROI and harden your endpoints against malwares
e.g., Ransomware, Trojan, Worm, etc.
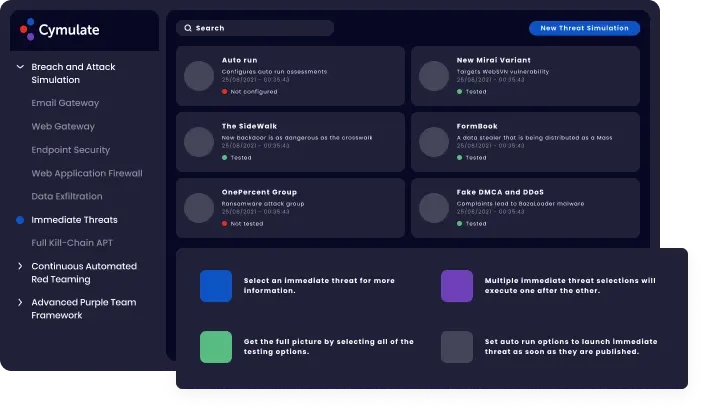
Immediate Threat Assessment:
The results of this assessment provide a clear answer to the risk, any given immediate threat (near zero-day or trending malware) creates. Do they exploit existing vulnerabilities that are present on endpoints in the network? And are security controls able to detect or block these threats? – The assessments use real malware samples but are constructed to run in production safely.
Benefits:
It takes out any ambiguity in controls detection, protection or response capabilities against specific threats. It also validates the SIEM/SOAR and SOC capabilities in detection, alerting and response to real world attacks.
Data Exfiltration – DLP Assessment:
It measures the effectiveness of your defence in protecting financial, personal, medical records, business critical information, source code, and any other sensitive data to protect your brand against data breach and damages.
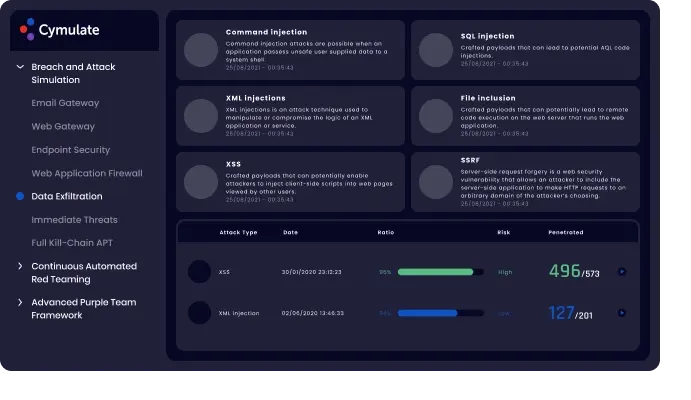
Benefits:
It takes out any ambiguity in controls detection, protection or response capabilities against specific threats. It also validates the SIEM/SOAR and SOC capabilities in detection, alerting and response to real world attacks.
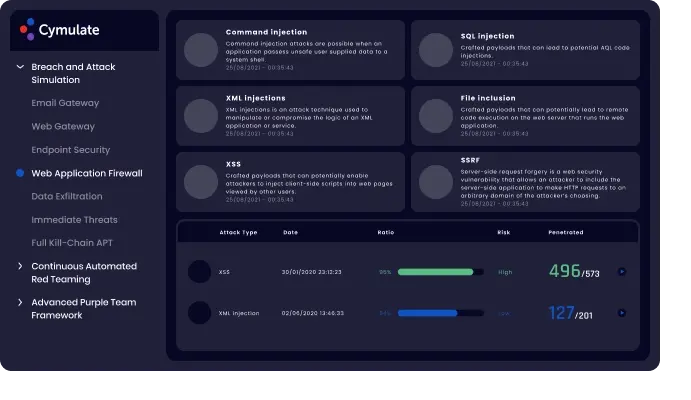
Web application Firewall Assessment:
It tests your WAF configurations and effectiveness in detection and protection against web attacks such as XSS, CSRF, SQLi, brute force, denial of service and many other attack types.
Benefits:
It measures your staff protection level while browsing internet and the ROI of your web protection capabilities.
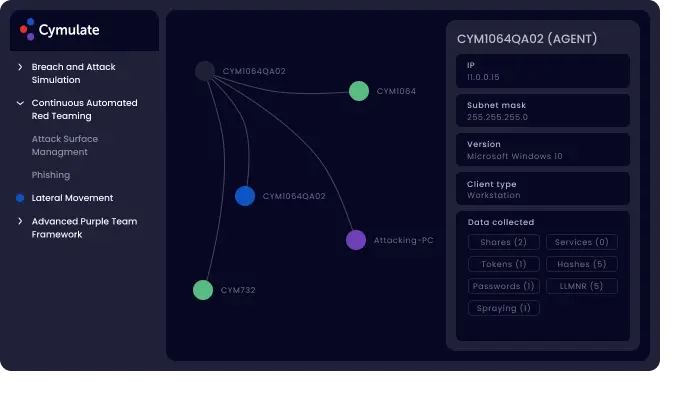
Network Security Assessment – Lateral Movement:
It tests your network threat protection measure’s configuration and effectiveness in detecting lateral movement and compromise attacks. The results of this test are presented in an interactive graphic diagram that shows the attacker’s path and details both the attack and spread methods.
Benefits:
Measure your protection against attacks such as ransomware, large scale data breach and complete business disruption.
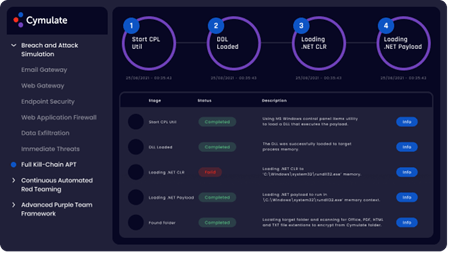
Full Kill-chain Advanced Persistent Threat (APT) assessment:
In this test, APT stages are launched sequentially, from a simulated attack on the email or web gateway, followed by endpoint security. The module challenges the organization’s network policies, trying to move laterally, launch ransomware and exfiltrate predefined sets of data (PII, medical records, payment details), testing DLP controls. – This includes real-world APT attacks launched by well-known APT groups, such as FIN8, Cobalt Group, APT38, Silent Librarian and many others.
Benefits:
Measure the risks and have a realistic view of your whole defensive capabilities against advanced threats, and proactively minimise those risks including data breach, business disruption, financial loss and brand damage.
- Lightweight agent, running on a single machine
- Safely perform attack simulations in your environment
- Allows you to choose which attack vectors you wish to simulate
- Takes less than 5 minutes to set up
- Provides immediate actionable insights on your security posture
Get a FREE demo and a trial
Automated Red/Purple Teaming:
It provides and open attack framework to craft and automate red and purple team exercises that leverage and scale adversarial expertise. You can easily craft and launch attack scenarios, auto correlated with security control findings, to assess your breach detection and incident response capabilities.
How it works:
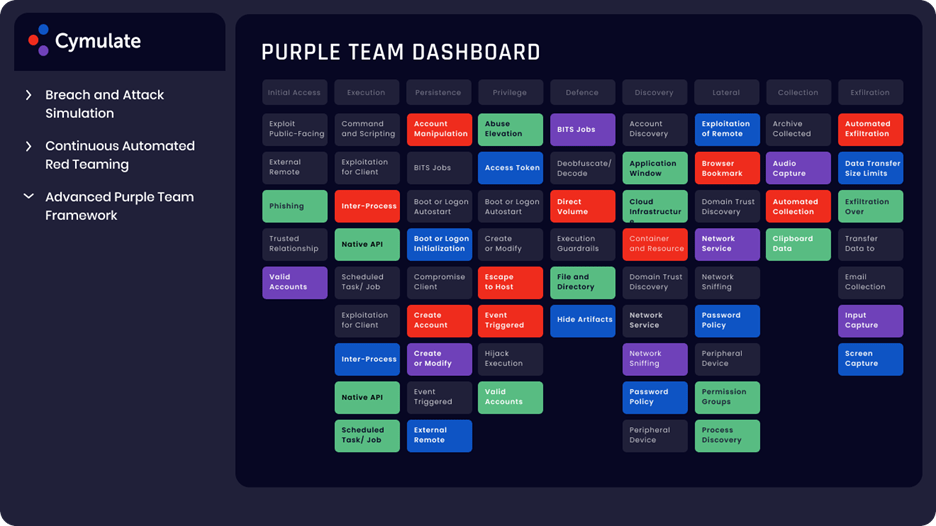
- Identify systematic weaknesses and security drift on MITRE ATT&CK Navigator and/or heat map
- Improve IT and cyber security hygiene
- Optimize protections and detection capabilities
- Continuously improve people-skills, incident response and threat hunting processes
- Lightweight agent, running on a single machine
- Safely perform attack simulations in your environment
- Allows you to choose which attack vectors you wish to simulate
- Takes less than 5 minutes to set up
- Provides immediate actionable insights on your security posture
Get a FREE demo and a trial
